Social Engineering Breaches
Malicious actors have a greater chance of successfully breaching a network infrastructure through social engineering than through traditional network/application exploitation. To help you prepare for this type of attack vector, we use a combination of Human and Electronic methodologies to simulate attacks. Human-based attacks consist of impersonating a trusted individual in an attempt to gain information and/or access to information or the client infrastructure. Electronic-based attacks consists of using complex phishing attacks crafted with specific organizational goals and rigor in mind. Encyphr customizes a methodology and attack plan specifically for your organization.
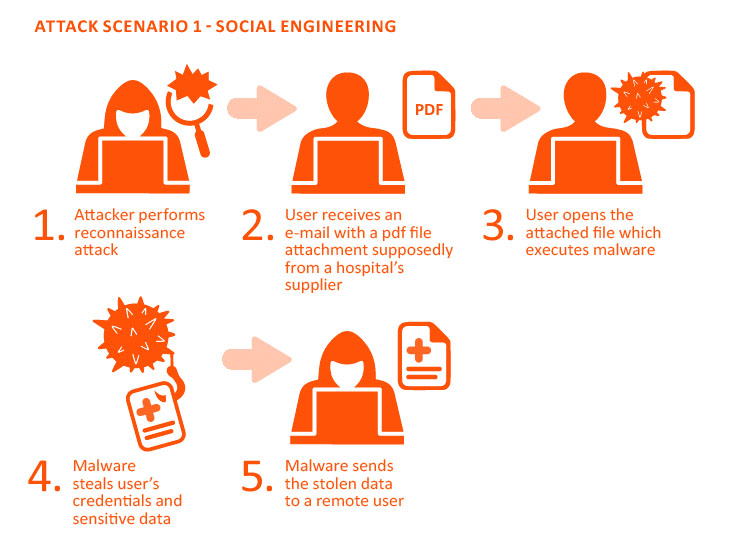
Human Social Engineering
The Human category of Social Engineering includes infectious media drops, physical security, dumpster diving, impersonation, and other attacks that require a physical presence. This is a type of testing that includes far too many variables for us to publish a flat price. Please contact us for a discussion of your requirements, and we'll provide a quote. Human Social Engineering is usually conducted in conjunction with an Internal engagement.
Electronic Social Engineering
The Electronic category includes email based spear-phishing attacks and other electronic attacks intended to bait network and security personnel. This testing requires a great deal of research on individual targets to be effective, and also requires serious attention to morale considerations and safety considerations, especially where electronic payloads are involved. Electronic Social Engineering is the type of Social Engineering indicated within our pricing. It is usually conducted in conjunction with an External engagement.

What is the Purpose of Social Engineering?
A social engineering test is a simulated attack from the perspective of a bad actor, such as a malicious hacker. The purpose is to simulate a cyber security in a way to circumvent traditional security protocols. It’s an attack and attempt to uncover security vulnerabilities that might otherwise be discovered by hackers. This type of attack provides valuable insight into the security posture of assets and the opportunity to address them before hackers are able to cause serious damage by exploiting them.
Hackers who use social engineering are constantly coming up with new means of attack; that’s why it’s so important to work with third-party testing professionals who are on the cutting edge of the latest attack trends, rather than relying on a DIY social engineering approach alone.

